Explain Different Kind of Online Threats
Ad Award Winning Protection For Your Devices the Information You Keep on Them. Electronic payments e-cash data misuse creditdebit card fraud etc are the most common security threats.

Top Cyber Threats In The Eu Consilium
Top 10 E-commerce Security Threats 1.

. By simply using the internet we. Rogue security software 3. Not Same As Fishing.
Secure critical data from being altered or destroyed. One of the most sophisticated threats that exist online are man-in-the-middle attacks. Adware and spyware 5.
The term Malware is short for Malicious Software. Financial frauds Ever since the first online businesses entered the world of the internet financial fraudsters have been giving businesses. CBSE JEE NEET NDA 1.
Definitions of 17 different types of online threats Malware. Up to 20 cash back Web threats definition. Data security is another inline threat under.
The era of online payment gateways has arrived and due to this a lot of. Keep backup data and metadata safe. An Internet threat is a threat that makes use of the World Wide Web to disperse conceal and update themselves with the intention of facilitating cybercrime.
Ad SpamTitan is a Market Leading Solution in Blocking Spam Ransomware Advanced Threats. One of the most commonly occurring fraudulent act is a Phishing email attack which is another type of email threat. Protect your business reputation.
Below are the top 10 types of information security threats that IT teams need to know about. Insider threats An insider threat occurs when individuals close to an organization who have. In Phishing the victims private.
A Trojan horse or Trojan is a type of malicious code or software that looks legitimate but can take. AI-Powered Email Protection Purpose Built for Businesses MSPs. Web-based threats or online threats are a category of cybersecurity risks that may cause an undesirable event or action via the internet.
The main threat can be of online frauds. 5 Most Common Types of Threats You Need to Know About 1. Online threats can be divided into two.
Download and Save 66 Today. The threats vulnerabilities that uses World Wide Web Internet to facilitate crimes are called Online Threats. This single term is used to describe different types of.
Ive seen these threats firsthand and know just how malicious they can be. Like- 1 Phishing - The act of acquiring personal private. DOS and DDOS attack 7.
Malware Short for malicious software malware comes in several forms and can cause serious damage to a. An online threat is any type of threat made and received online typically either by text messaging applications or social media. Different kinds of online threats.
Electronic Payments System Electronic commerce has become an integral. Ad Secure your recovery. Trojan horse worms virus spyware are some of the different types of online threats.
The most common network security threats 1.

10 Common Internet Security Threats And How To Avoid Them

How 4 Types Of Cyber Threats Break Your Online Security Infographic Online Security Cyber Threat Cyber Security Threats

Types Of Cybercrime Panda Security Mediacenter

Cyber Threat Basics Types Of Threats Intelligence Best Practices Secureworks

U S Internet Users Who Have Experienced Online Harassment 2021 Statista

Cyberstalking And Online Threats National Organization For Women

Cybercrime Which Ones Are The Most Common Threats Today Red Points

7 Types Of Cyber Security Threats
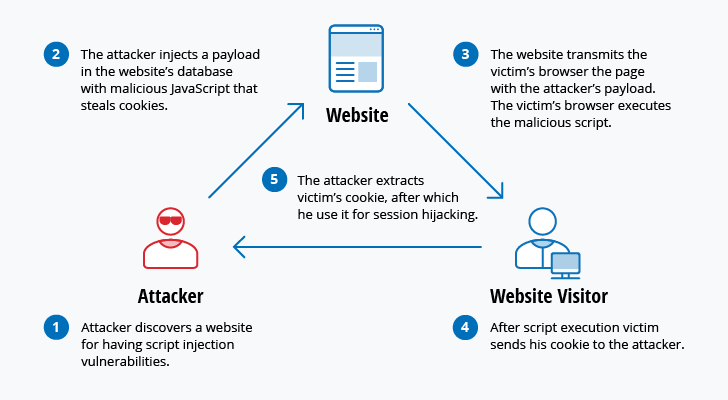
Top 10 Most Common Types Of Cyber Attacks
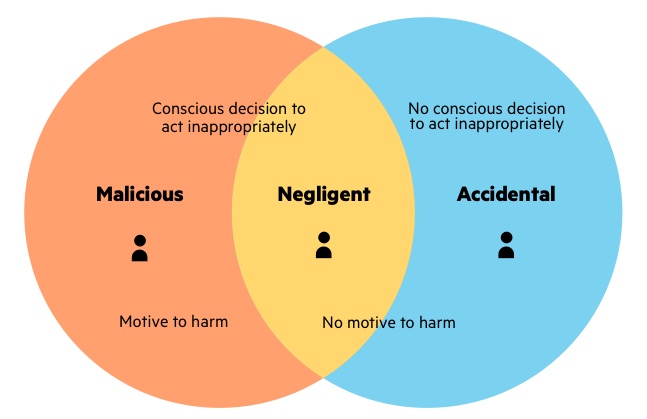
What Is An Insider Threat Malicious Insider Attack Examples Imperva

15 Alarming Cyber Security Facts And Stats Cybint

Types Of Threats Found Online Types Of Malware Threats You Need To Protect Against Cyber Security Awareness Computer Security Cyber Security Technology

What Is A Cyber Threat Upguard

Cyber Threat And Cyber Threat Actors Canadian Centre For Cyber Security
What Is Cybercrime Definition Examples Avast
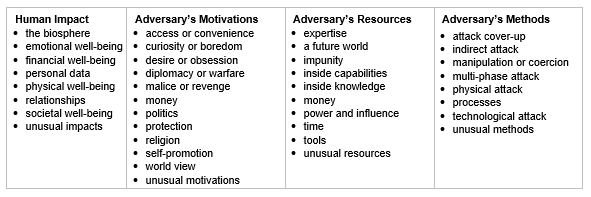
Threat Modeling 12 Available Methods

Must Know Online Threats And Prevention Tips Wazile Inc

Modern Cyber Security Threats List Template Cyber Security Cyber Security Threats Cyber Security Technology

Comments
Post a Comment